As countries progress in their digital transformation journeys, establishing trust in digital interactions becomes increasingly vital. Public Key Infrastructure (PKI) is a critical enabler of secure and trustworthy electronic transactions, constituting a key component of a country’s digital public infrastructure. This policy note focuses on how governments can effectively implement PKI at a national level—complementing previous work on electronic signatures—by delving into the policy, institutional, technology, and governance enablers necessary for PKI deployment. The aim of this note is to guide policymakers in creating a secure, sustainable, and trusted PKI ecosystem that provides a foundation for the digital transformation of government and the economy.
This note is designed to be read alongside the companion policy note on electronic signatures,1 which explains the role of PKI in implementing cryptographically secured digital signatures within a national electronic signature framework. The present note extends this analysis through practical guidance on implementing PKI at scale, ensuring government efforts complement private sector investments. By surveying different approaches, the note showcases diverse strategies that policymakers can draw from when designing and building their own national PKI ecosystems. This analysis is illustrated through illustrative case studies drawn from countries and organizations across various regions and income levels, namely India, Brazil, the United States, South Korea, Estonia, Saudi Arabia, The Netherlands, France, the United Kingdom, and Lebanon, as well as the European Union and the International Civil Aviation Organization (ICAO).
PKI Fundamentals
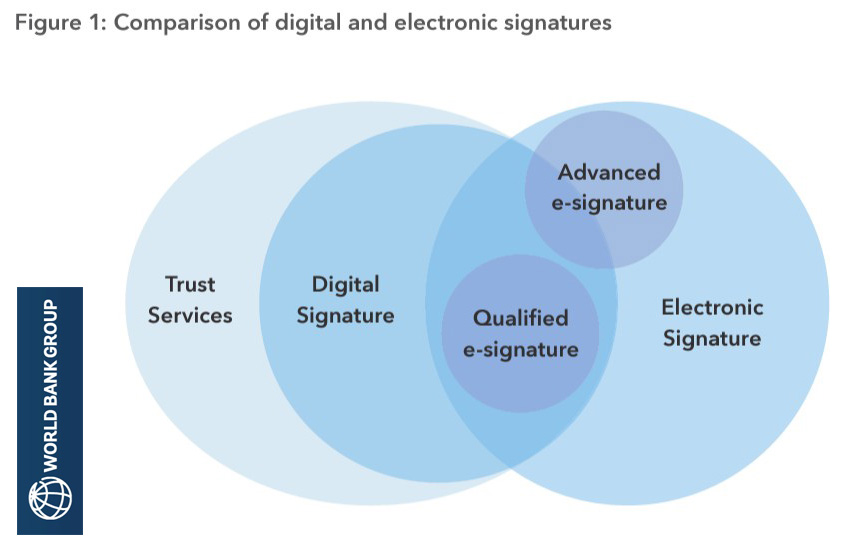
Digital signatures leverage public-key cryptography to ensure the integrity of digital documents and data. Although based on public-key cryptography, PKI is not a technology. PKI extends cryptographic technologies with complementary policy, organizational, and process elements to enable secure deployment of digital signatures in real-world applications. It provides a system for managing digital certificates and public-private key pairs, which are essential for securing online transactions, protecting data integrity, and implementing high-trust electronic signatures.
Implementing a national PKI is a complex endeavor that extends beyond technology. It involves establishing a comprehensive ecosystem encompassing core components, hierarchical structures, operational processes, governance frameworks, and strategies to promote adoption and manage liability. The PKI is designed so that the policy, operational, governance, and technological aspects, taken together, provide robust assurance that private keys are securely issued and managed, public keys are validated and trusted, and compromised keys can be efficiently revoked.
PKI Implementation
Components and architecture. The core components of a PKI include the digital certificates issued to signers, Certificate Authorities (CAs) that issue them, and the Registration Authorities (RAs) that verify the identity of signers before doing so. Other components such as revocation lists and central directories provide a centralized and trusted source of information on certificate validity. These components work together within a hierarchical architecture to establish an unbroken chain of trust from the root CA down to individual signed documents and data.
Operations and policy. Effective PKI implementation requires robust operational processes, including certificate issuance, registration and identity verification, key management, certificate renewal and revocation, incident monitoring, and disaster recovery. Managing these operations demands meticulous attention to detail to maintain the integrity, availability, and security of the PKI system, ensuring it functions seamlessly and remains resilient against threats. To maintain trust, a high level of transparency about these operational elements is required, as well as strict adherence to a set of policies and standard operating procedures.
Interoperability and federation. It is common for multiple PKI implementations to coexist for various reasons, including legacy systems, differing jurisdictions and institutional mandates, specific regulatory requirements, and the involvement of public and private sector actors. In such cases, trust in one PKI can be extended to others using a variety of federation approaches. Technology-based federation techniques include bridge certification and cross-certification, while non-technology approaches include adherence to common standards and the implementation of a trusted central broker. Whatever the approach, federation allows independent PKIs to interoperate, ensuring that certificates issued under one PKI are recognized and trusted by others. In practice, many countries use federation to allow various PKI implementers to operate within their mandates while contributing to an interoperable ecosystem.
Governance frameworks. Robust governance is essential to ensure trust and interoperability within the PKI ecosystem. Clear legal and regulatory frameworks should define roles, responsibilities, and standards for all stakeholders. This includes policy formulation, compliance mechanisms, supervision, and dispute resolution processes. Effective governance maintains public trust by ensuring that the PKI operates securely, effectively mitigates risks associated with security breaches, and provides for accountability in cases where something goes wrong.
Deployment models and sourcing strategies. Governments face choices between insourcing and outsourcing PKI components based on capacity, cost-efficiency, and security considerations. The note surveys various implementation strategies from these case studies, showcasing how countries have insourced or outsourced different PKI functions to the private sector. Hybrid models that combine government control with private sector innovation are increasingly popular. Decisions on deployment models—whether on-premises, cloud-based, or hybrid—impact scalability, security, and compliance with regulatory requirements.
Driving adoption and engaging stakeholders. Merely providing digital certificates is not sufficient to ensure people use them. To drive adoption, PKI should be integrated into essential and widely used services, creating compelling use cases that demonstrate the value of secure digital interactions. To make this happen, it is necessary to ensure a simplified and accessible user experience, relegating the technical complexity of PKI operations to the background. Ongoing engagement with stakeholders—including government agencies, private sector entities, relying parties, and end-users—is critical for aligning the PKI system with evolving needs, ensuring flexibility, and building sustained public trust.
Recommendations
To successfully implement a national PKI ecosystem, it is recommended that governments first establish the strategic foundations of the PKI implementation, and then design a PKI architecture and governance framework that meets these strategic requirements, ensures scalability in the face of increasing demand, and promotes adoption through usability and integration into people’s lives. Specific recommendations include:
- Establish strategic foundations
- Integrate PKI development into the broader digital transformation strategy.
- Ensure PKI is part of a comprehensive electronic transactions framework, adopting a risk-based approach.
- Tailor the PKI ecosystem to local demand and digital maturity.
- Design for success
- Customize the PKI architecture based on contextual factors like use cases and institutional capacity.
- Focus on robust governance frameworks encompassing regulations, standards, and oversight mechanisms.
- Position the government as an enabler, fostering private sector participation and innovation.
- Ensure scalability
- Employ federated trust models to enhance interoperability and scalability.
- Leverage existing infrastructures, such as national ID systems and registration centers, to streamline PKI processes.
- Promote adoption
- Drive adoption by integrating PKI into essential services and improving user experience.
- Encourage market development for PKI services, lowering costs and fostering innovation.
- Maintain continuous stakeholder engagement to align the PKI system with user needs and build public trust.
Source: Worldbank
